This weekend I tried to setup a AWS VPN proxy in Tokyo, Japan. My main reason for doing so was I wanted to watch Netflix in Japan. I followed the instructions on this link: https://hackernoon.com/using-a-vpn-server-to-connect-to-your-aws-vpc-for-just-the-cost-of-an-ec2-nano-instance-3c81269c71c2 using OpenVPN.
But there were a couple of modifications I had to make to make this work:
-
You need to uncomment out two lines in /etc/openvpn/server.conf. Every configuration that starts with a ; is effectively a commented out configuration. One for something equivalent to:
push "route 172.31.0.0 255.255.0.0" push "dhcp-option DNS x.x.x.x" # Push your preferred VPN DNS - google eg. 8.8.8.8 push "block-outside-dns" (https://forums.openvpn.net/viewtopic.php?t=22039) - Check if there are any leaks or problems. I’ve checked the websites https://whatismyipaddress.com/proxy-check and https://ipleak.net/ for any traces of my original source ip. There was none.
-
You need a modified command like:
scp -i "Jvpn.pem" [email protected]:~/ .To transfer your generated ovpn file to your local directory
- Use Tunnelblick and the generated ovpn file to connect to your vpn. Make sure to look at the logs for any breaking issues.
So I do all these checks, and I was pumped to try out my new VPN so that I can watch some Netflix in Japan. Like Rick and Morty and Terrace House. So I login to Netflix, and try to start watching a show….
And then, I am greeted by this familiar friend:
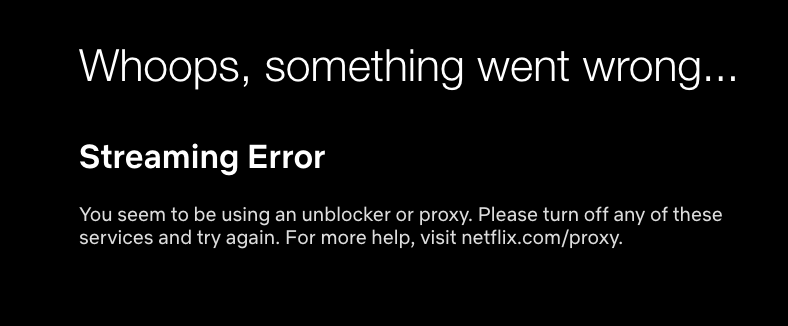
This would have been a happy ending if it worked. But it didn’t =(.
How are they finding out that I’m behind a proxy??!
- Apparently AWS has a public JSON of all their ip address ranges (https://ip-ranges.amazonaws.com/ip-ranges.json). The first elastic IP address I put in was on there, but the second one I got was not. Do they have another secret list? There’s really nothing I can do because companies buy blocks of ip addresses with their name on it… No matter what I do, they would still know that the ip is from amazon.com. Unless I go get another obscure cloud service provider to give me an ip…
- Suppose that the elastic ip address that I used is not on their radar. Do they still know that my account was registered in the U.S. and adjust accordingly? It’s not like one person can connect from the U.S. at 1 PM and suddenly connect from Japan at 5 PM. Unless they can teleport…
Anyhoo, I’m a little disappointed that I can’t go on Netflix Japan. If they are using some techniques that align with #2, then a VPN is virtually useless. It leads me to wonder if there are other sophisticated techniques to detect proxies. I wonder, if at the packet level, if there is a difference between a packet sent from the U.S. vs. a packet sent from Tokyo. Even just by timing, wouldn’t you be able to figure this out?
For example, this is a simple ping to Google. This is with vpn turned on and off:
#VPN ON
PING google.com (172.217.161.78): 56 data bytes
64 bytes from 172.217.161.78: icmp_seq=0 ttl=43 time=187.722 ms
64 bytes from 172.217.161.78: icmp_seq=1 ttl=43 time=186.720 ms
64 bytes from 172.217.161.78: icmp_seq=2 ttl=43 time=189.030 ms
64 bytes from 172.217.161.78: icmp_seq=3 ttl=43 time=186.826 ms
64 bytes from 172.217.161.78: icmp_seq=4 ttl=43 time=188.989 ms
64 bytes from 172.217.161.78: icmp_seq=5 ttl=43 time=186.898 ms
64 bytes from 172.217.161.78: icmp_seq=6 ttl=43 time=189.009 ms
64 bytes from 172.217.161.78: icmp_seq=7 ttl=43 time=199.305 ms
64 bytes from 172.217.161.78: icmp_seq=8 ttl=43 time=192.338 ms
#VPN OFF
--- google.com ping statistics ---
9 packets transmitted, 9 packets received, 0.0% packet loss
round-trip min/avg/max/stddev = 186.720/189.649/199.305/3.794 ms
PING google.com (172.217.161.46): 56 data bytes
64 bytes from 172.217.161.46: icmp_seq=0 ttl=48 time=164.479 ms
64 bytes from 172.217.161.46: icmp_seq=1 ttl=48 time=163.677 ms
64 bytes from 172.217.161.46: icmp_seq=2 ttl=48 time=166.483 ms
64 bytes from 172.217.161.46: icmp_seq=3 ttl=48 time=163.280 ms
64 bytes from 172.217.161.46: icmp_seq=4 ttl=48 time=163.296 ms
64 bytes from 172.217.161.46: icmp_seq=5 ttl=48 time=164.817 ms
64 bytes from 172.217.161.46: icmp_seq=6 ttl=48 time=162.720 ms
^C
--- google.com ping statistics ---
7 packets transmitted, 7 packets received, 0.0% packet loss
round-trip min/avg/max/stddev = 162.720/164.107/166.483/1.179 ms
(I know the ip is different, but they’re location check out to California).
If Netflix measures the round trip times of packets, calculate things like standard deviation, percentiles of packets, total response time between actions, etc and feeds it into some statistical model, they can easily figure out that there’s a high chance that this person is behind a proxy.
As for this VPN, unless I have a breakthrough, I guess I’ll be sticking to Netflix US for the time being. At the very least, I now have my personal VPN in Japan. The silver lining to all this is that my personal VPN is wicked fast =D.